Your clients need assurance that the private and sensitive data they entrust to you is secure. At Mauldin & Jenkins, our team of experts is dedicated to providing a comprehensive and extensive report of your system and organization controls.

Healthcare providers

software as a service (saas) companies

payment processors
SOC for Cybersecurity
The new AICPA SOC for Cybersecurity is based on the Trust Service Principles of Availability, Integrity, and Confidentiality but is a general, openly shared report. The SOC for Cybersecurity uses 19 different description criteria (based on the aforementioned TSPs) and is specific to reporting on an entities efforts and operating effectiveness of its controls over its Cybersecurity Risk Management Program (CRMP). The SOC for Cybersecurity was designed specifically to work with the AICPA's CRMP, which is another type of Cybersecurity Framework. Other popular Cybersecurity Frameworks such as: HITRUST CSF, NIST 800-53 CSF, COBIT 5, and ISO 27001/2, exist and can still be used in a SOC for Cybersecurity engagement.
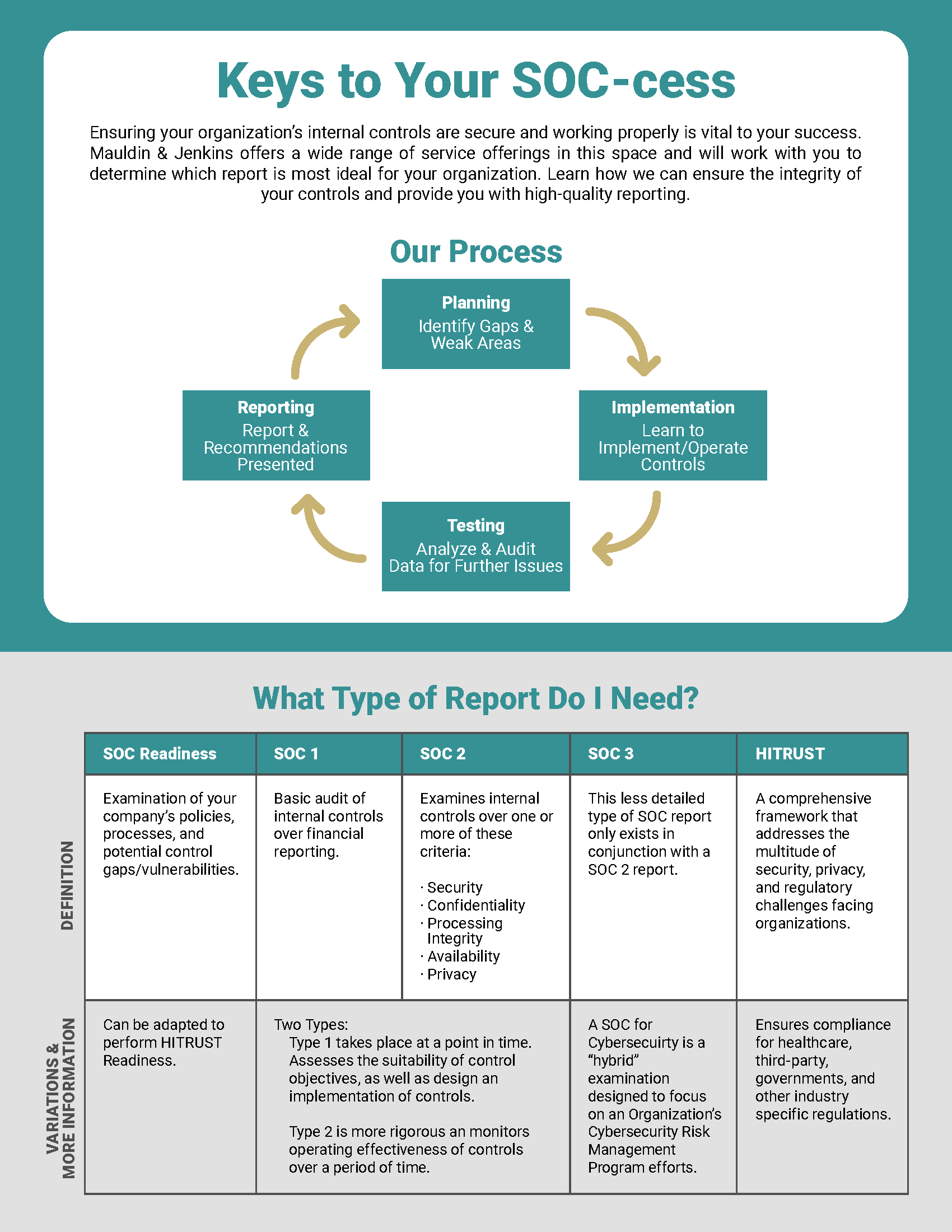
Service Organization Controls (SOC) Reports
SOC 1 Reports
Reporting on controls at a Service Organization Relevant to User entities' Internal control over financial Reporting
This meets the needs of user entities' managements and Auditors as they evaluate the effect of a service organization's controls on a user entity's financial statement assertions.
These reports are important components of user entities' evaluation of their internal controls over financial reporting for purposes of compliance with laws and regulations and for when user entity auditors plan and perform financial statement audits.
SOC 2 Reports
Reporting on Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy (SOC 2®)
For those who need to understand internal control at a service organization as it relates to security, availability, processing integrity, confidentiality, or privacy.
These reports can play an important role in oversight of the organization, vendor management programs, internal corporate governance and risk management processes, and regulatory oversight. Stakeholders who may use these reports include management or those charged with governance of the user entities and of the service organization, customers, regulators, business partners and suppliers, among others.
SOC 3 Reports
Trust Services Principles, Criteria, and Illustrations
Designed to accommodate users who want assurance on a service organization’s controls related to security, availability, processing integrity, confidentiality or privacy but do not have the need for the detailed and comprehensive SOC 2® Report. It can be used in a service organization’s marketing efforts.
SOC Gap Analysis/Readiness Engagement
A consulting engagement aimed at helping a client prepare for a SOC for Cybersecurity, SOC 1, or SOC 2 Audit.




